# OneLogin
Log in to your OneLogin (opens new window) account and head to the dashboard.
# Create OpenID Connect App
Click Apps on the top menu. Select the Add apps menu item.
On the Find Application page, search for openid. Select Openid Connect by OneLogin, Inc.
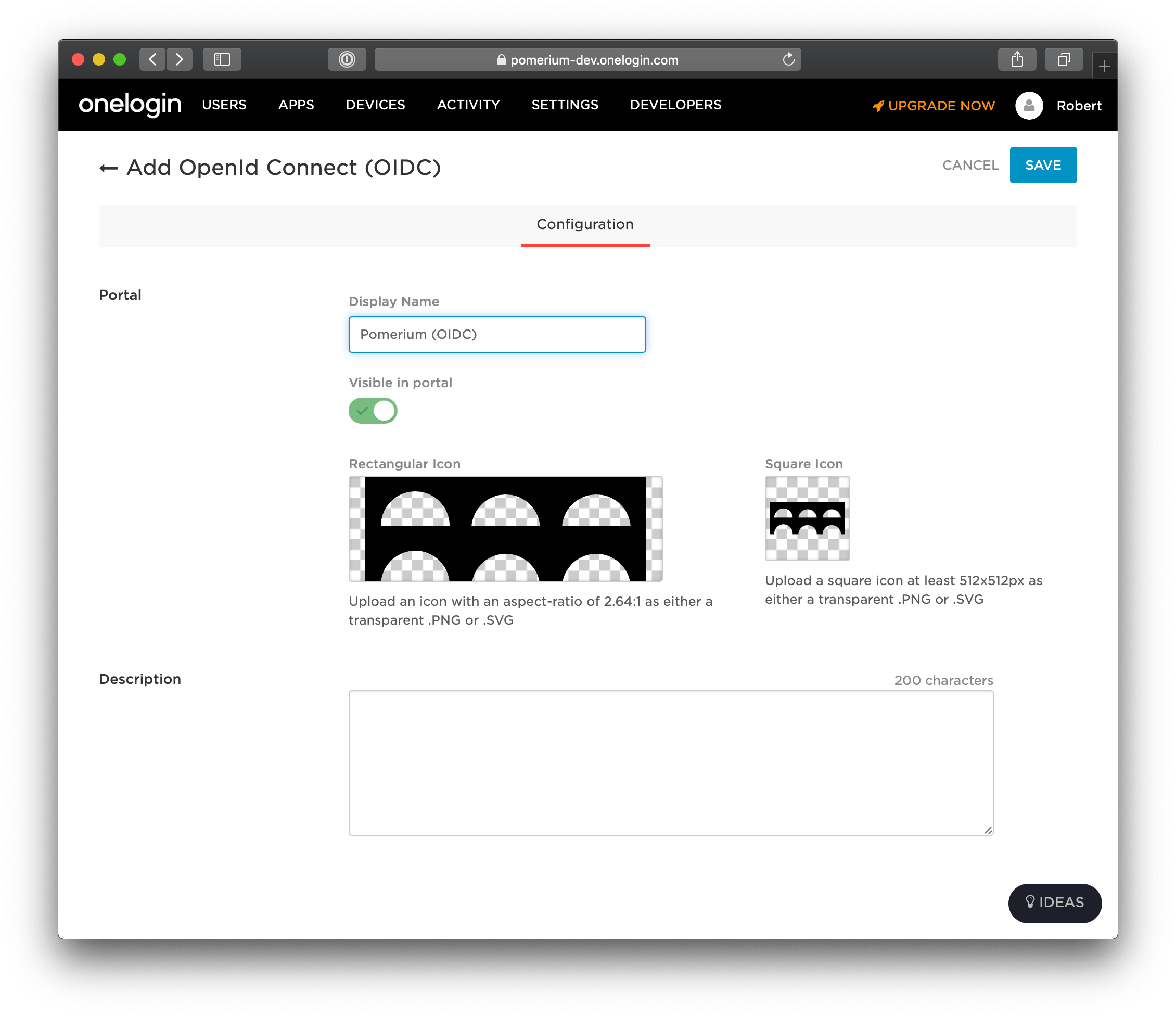
On the App Configuration page, name the app and select a logo. Select Save.
Next, set set the Redirect URI's setting to be Pomerium's redirect url https://${authenticate_service_url}/oauth2/callback.
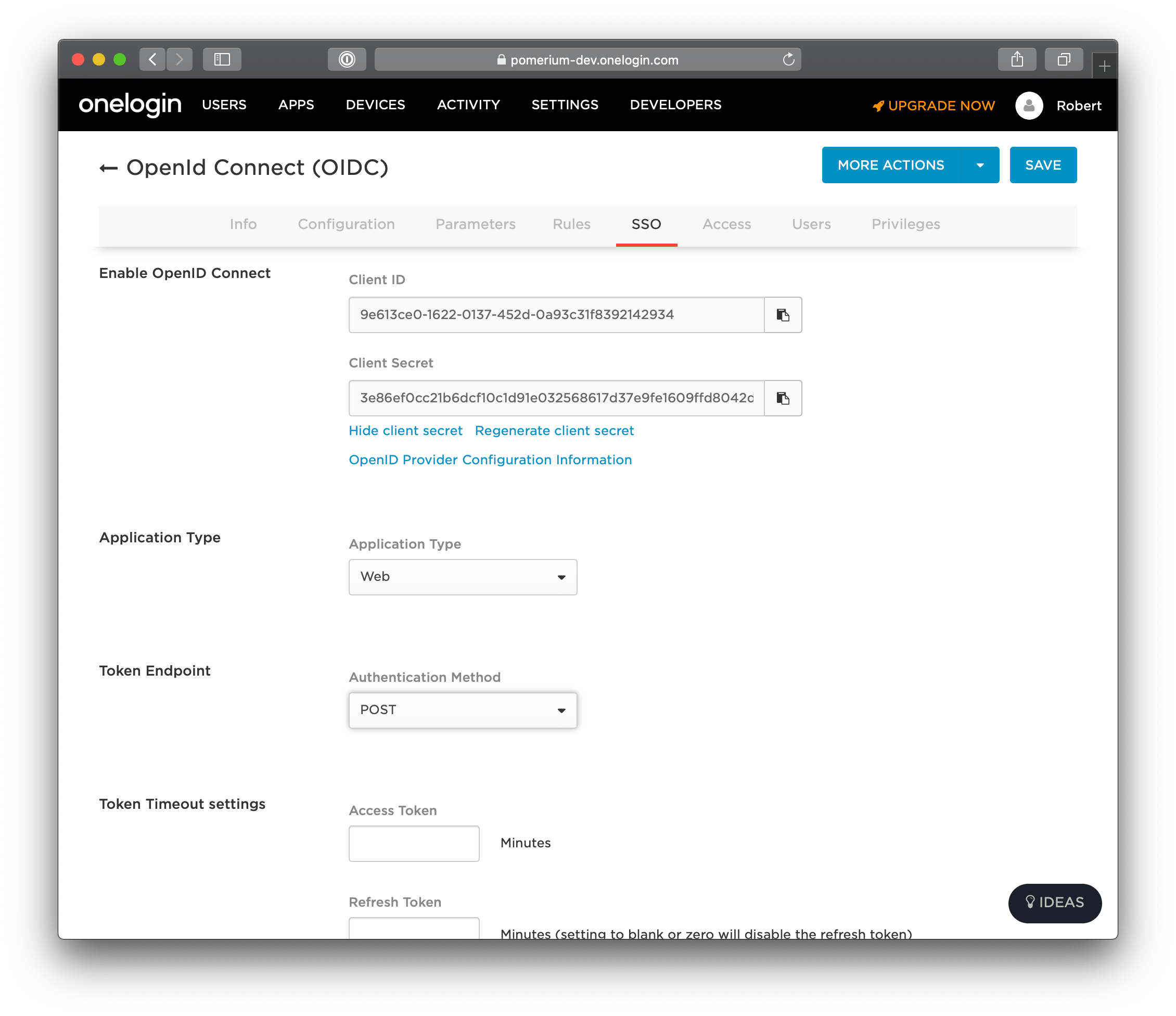
Go to the SSO page. This section contains the Client ID and Client Secret you'll use to configure Pomerium.
Set the application type to Web and the token endpoint to be POST.
Under Token Timeout settings set Refresh Token to 60 minutes (or whatever value makes sense for your organization). Note, however, if you don't enable refresh tokens the user will be prompted to authenticate whenever the access token expires which can result in a poor user experience.
# Service Account
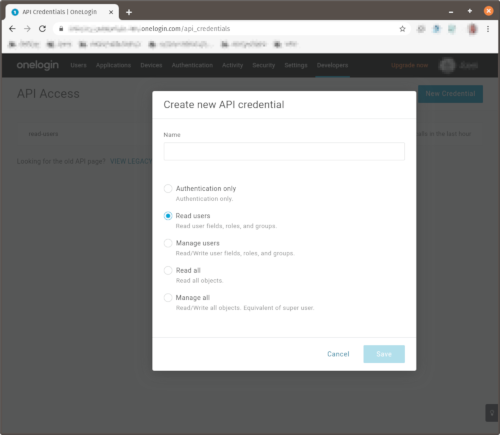
To use allowed_groups in a policy an idp_service_account needs to be set in the Pomerium configuration. The service account for OneLogin uses a different client ID and client secret from the one configured above. It can be created with "Read users" access under Developers/API Credentials:
The format of the idp_service_account for OneLogin is a base64-encoded JSON document:
{
"client_id": "...",
"client_secret": "..."
}
A Group's ID (opens new window) will be used to affirm user group membership.
# Pomerium Configuration
IDP_PROVIDER="onelogin"
IDP_PROVIDER_URL="https://openid-connect.onelogin.com/oidc"
IDP_CLIENT_ID="9e613ce0-1622-0137-452d-0a93c31f8392142934"
IDP_CLIENT_SECRET="3e86ef0cc21b6dcf10c1d91e032568617d37e9fe1609ffd8042d3c25a560c36c"
After reloading Pomerium, you should be able to see any login events from your OneLogin events dashboard.